Modernize the Work Experience
Modernize the Work Experience As AI rapidly transforms industries, businesses must adapt quickly to stay competitive,…
Cybersecurity stands as the single most critical pillar in any business’s IT infrastructure strategy. At CB Tech Hub, we are unwavering in our commitment to ensuring that you remain well-informed and well-prepared to safeguard your business against the ever-evolving landscape of cyber threats. We are your dedicated frontline defenders, consistently delivering the freshest insights, the most cutting-edge protective measures, and a spotlight on emerging companies that are shaping the cybersecurity market.
In an era where cyberattacks continue to rise in frequency and sophistication, your business’s digital fortifications have never been more crucial. We recognize that navigating the complex and ever-shifting terrain of cybersecurity can be challenging, but that’s where we come in. Cybersecurity market is constantly evolving, with new and innovative companies entering the scene. We serve as your beacon in this dynamic space, introducing you to exciting startups and cutting-edge solutions that have the potential to revolutionize your cybersecurity posture.

At CB Tech Hub, we are committed to delivering you the latest information in a timely and easily digestible manner. Count on us to keep you informed about the latest cybersecurity trends, best practices, and emerging technologies.

Modernize the Work Experience As AI rapidly transforms industries, businesses must adapt quickly to stay competitive,…

Why an Accelerated PC Refresh Cycle Makes Sense today Increasing security vulnerabilities, Windows 11 upgrades, and…
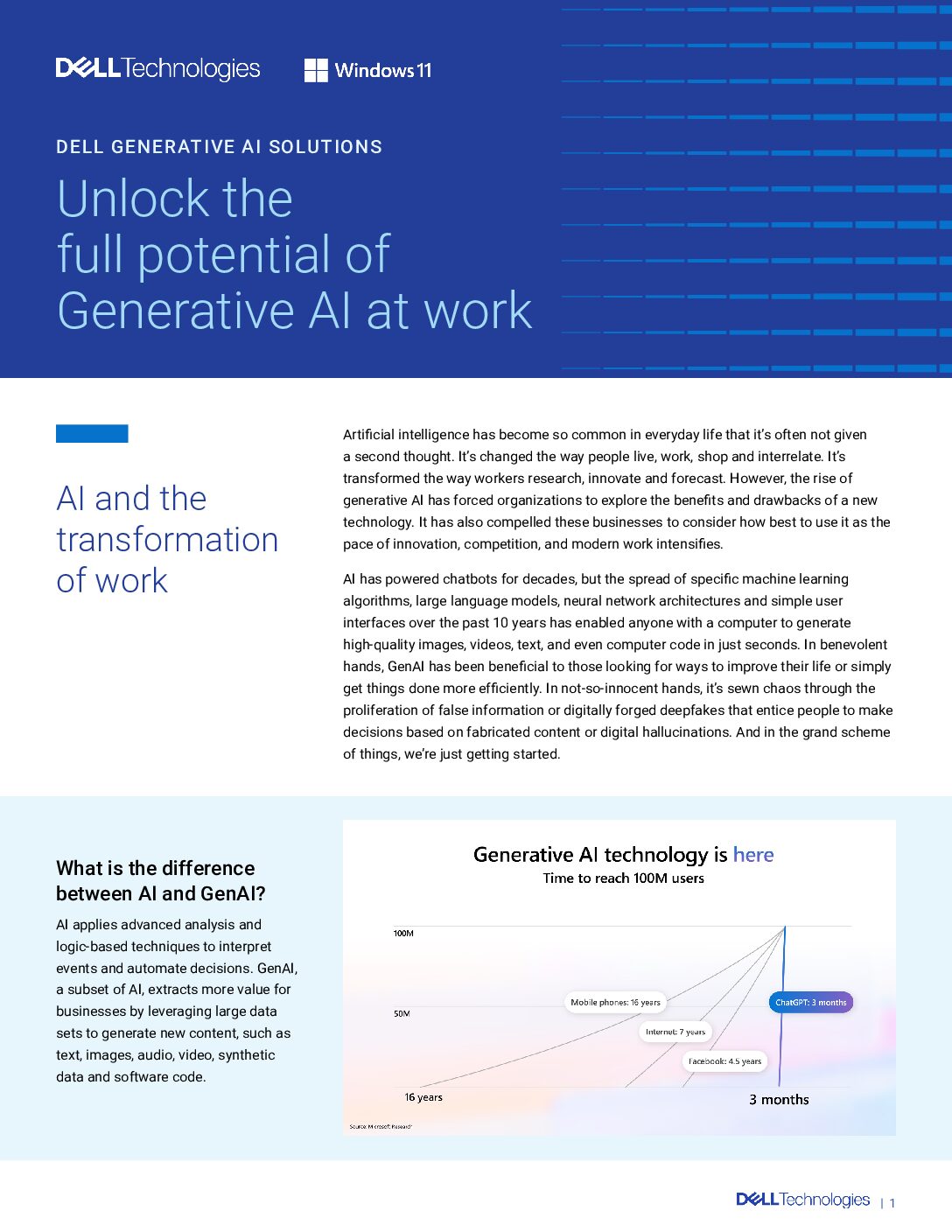
Unlock the full potential of Generative AI at work Artificial intelligence has become so common in…
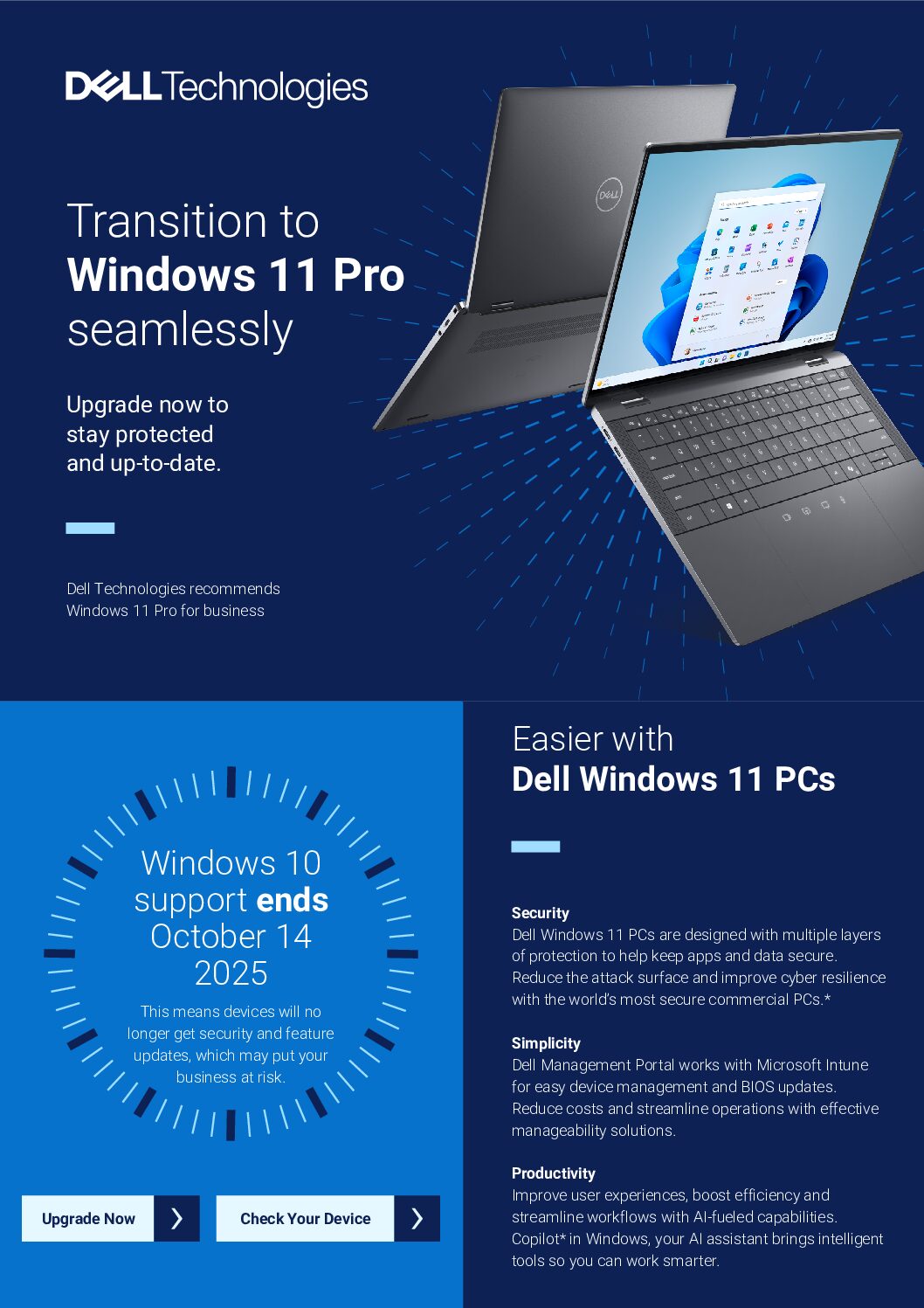
How to prepare for Windows 10 end of support by moving to Windows 11 today Dell…
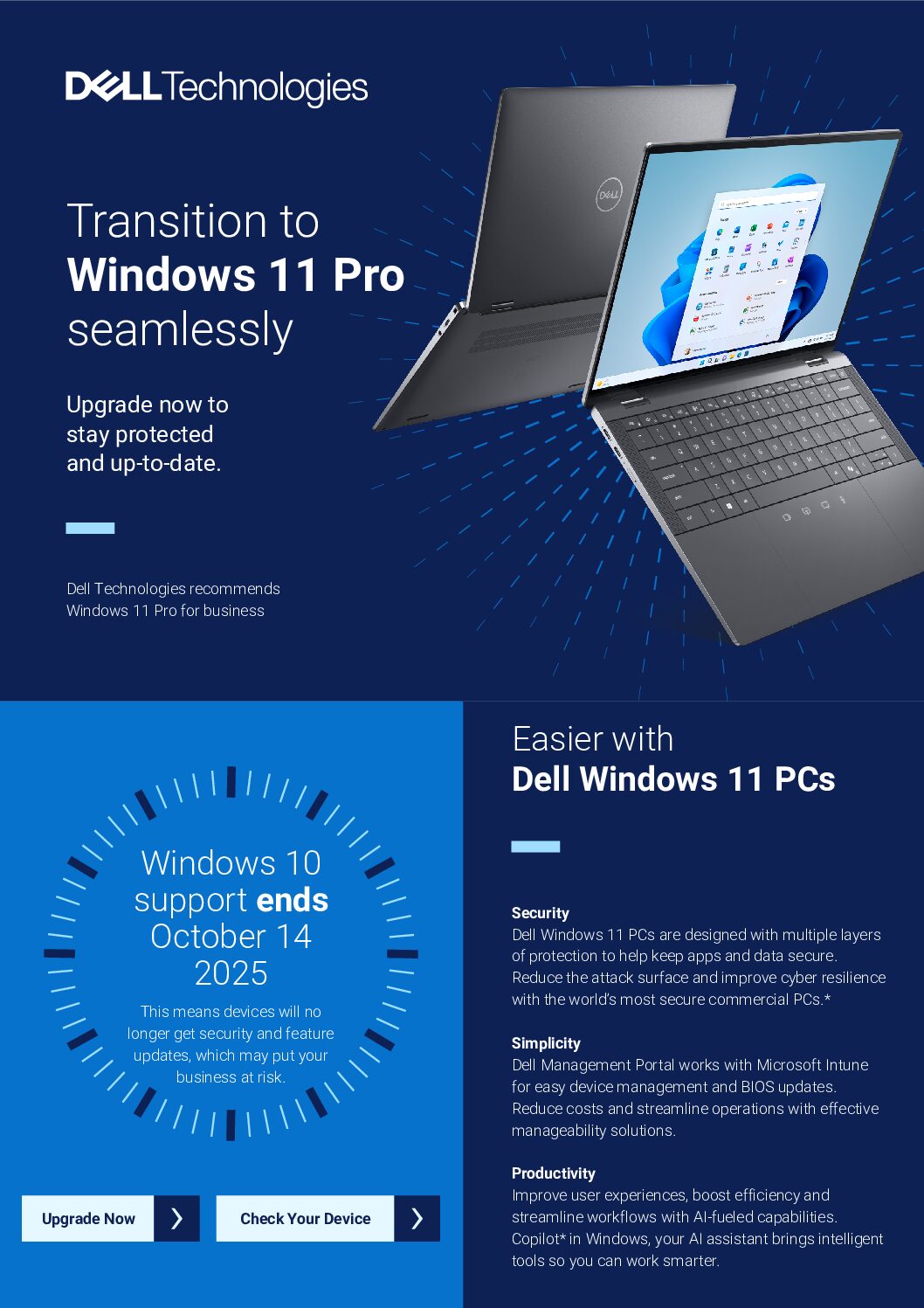
Transition to Windows 11 seamlessly Unleash the full potential of your organization with innovations and solutions…

Modernize the Work Experience As AI rapidly transforms industries, businesses must adapt quickly to stay competitive,…

Unlock the full potential of Generative AI at work Artificial intelligence has become so common in…

boosting productivity and security with modern devices pT comparative study As companies navigate the era beyond…

Why an Accelerated PC Refresh Cycle Makes Sense today Increasing security vulnerabilities, Windows 11 upgrades, and…